How safe is Microsoft 365 service? Learn how to keep your Microsoft 365 operation environment safe from malware, unauthorized access, and cyberattacks.
How safe is any Microsoft 365 service? Is your Microsoft 365 operation environment safe - from malware, unauthorized access, and cyber attack?
Yes! Microsoft 365 has cybersecurity features, including malware protection and compliance with pre-set policies, such as blocking certain file-type attachments.
But most of the protection services don't come by default. Microsoft 365 protects business data against cyber attacks, but you must follow the guidelines and comply with its security features.
So, in this article, we address the top security features to protect your Microsoft 365 for Business.
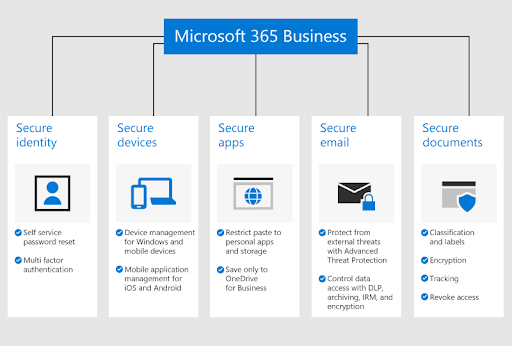
Does Microsoft 365 Provide Security?
Also, "How secure is Microsoft 365 environment?

Microsoft 365 is a highly secure platform with over 1 Million businesses globally. It includes various robust security capabilities across 4 vectors:
Let's see what they offer:
- Identity & access management. To protect Microsoft 365 user identities and devices and access critical business data/resources based on risk levels.
- Threat protection. Protects users and devices against advanced threats and helps businesses recover quickly when attacked. The Microsoft 365 treat protection solutions include Microsoft Defender, Microsoft Cloud App Security, and Defender for Endpoint.
- Information protection. It helps ensure that only authorized people see emails and vital documents.
- Security and risk management. This gives IT staff control and data and information security tools visibility.
Each security vector is protected by robust security features deployed based on every Microsoft 365 license type. Most apply to:
- Microsoft 365 Business Basic
- Microsoft 365 Business Standard
- Microsoft 365 Business Premium
Summary: Microsoft 365 for Business includes many security capabilities, such as anti-phishing, anti-spam, and anti-malware protection. Furthermore, Microsoft 365 Business Premium includes more capabilities, such as device security, advanced threat protection, and information protection.
Top 11 Microsoft 365 Security Features and Compliance to Secure your Data
Let's look at the following top Microsoft 365 security and compliance features for businesses:
#1. Use Multi-factor Authentication
Multi-Factor authentication (MFA), including 2FA, is a 2-step verification method that provides an added protection layer during the login process into a device, website, or application. It requires people/users to use a code or authentication app on their phone to sign into Microsoft 365, making it a critical first step to protecting your Microsoft 365 and business data. For example, you can use a password combination of a passcode and biometrics (retinal or fingerprint scan) to confirm your identity and authority. MFA/2FA can prevent hackers who know your password from taking over.
Microsoft 365 has 2 MFA options:
- Built-in 2FA. IT admins can use 2FA to activate users at different levels with options for a second verification method, such as biometrics, passcode, etc.
- Azure MFA. This is a security add-on that companies can add to their Microsoft 365 at an additional cost to give them more control.
The company's Microsoft 365 admin, internal or external, manages its MFA policies and procedures.
#2. Protect Admin Accounts
Microsoft 365 Administrator accounts (a.k.a admins) have extra elevated privileges, making them more susceptible to unauthorized access attempts and cyberattacks. It is important to set up the right number of admin accounts for your Business, separate them from user accounts, and manage them well. Also important is adhering to the information security principle of least privilege, meaning granting users and app access only to the info, data, and operations they require to complete their jobs.
#3. Comply with Preset Security policies
Your Microsoft 365 subscription includes pre-set security policies that use recommended settings for antimalware, antispam, and anti-phishing protection. Sticking to these policies and complying with their security protection provisions is important. Sometimes you may need to tweak the security provisions to align with your business and security demands. It's important always to ensure that the policies are on and working.
#4. Use Strong Password Policies
A business's password policies govern its users, IT staff, and network admins to enhance its device, network, website, and data security. This includes using strong password characteristics such as length and the allowed/disallowed characters.
Microsoft 365 and Azure AD (cloud-only accounts) have predefined password policies that IT/Network admins cannot change. These include password length, complexity, characters, and expiry duration. The policies advise users/admins to avoid using characters like names, dates of birth, and more personal details and avoiding reusing passwords for stronger password security.
#5. Protect all Devices and Use Mobile Device Management (MDM)
Every device at your Business is a possible attack avenue into your network or data and must be configured properly, even those personally owned devices (BYOD) used for work. Protecting these endpoints means protecting your Business.
Microsoft 365 offers Mobile device management (MDM). MDM is a software (toolset) and methodology to monitor and manage mobile devices accessing enterprise data (sensitive).
Note: MDM isn't a provision to help businesses spy on employees but only to control access to its sensitive data, including management of the Bring Your Own Device (BYOD) devices.
The common MDM components are:
- Device inventory
- Tracking
- Password enforcement
- Identity and access management
- App whitelisting/blacklisting
- Endpoint security
- Remote wipe
- Encryption
- And more.
A company can choose the Microsoft 365 built-in MDM or Microsoft Intune for more control over enterprise data.
#6. Defender for Microsoft 365
Microsoft 365 Defender is a cloud-based cybersecurity service that provides integrated protection against sophisticated attacks and malware. It's designed for email and other Microsoft 365 protection needs as a unified pre- and post-breach cybersecurity defense suite.
The Defender for Office 365 suite is connected to Microsoft's database to analyze endpoints and evaluate texts, files, emails, or links for any malware potential. The various services Microsoft 365 Defender offers include end-to-end encryption, threat investigation, threat protection policies, and reports. It offers these services in 3 security services:
- Exchange Online Protection (EOP)
- Defender for Office 365 Plan 1 (P1)
- Defender for Office 365 Plan 2 ( P2)
Check out your plan to find out which services your Microsoft Defender has.
#7. Encrypted Email
Microsoft 365 business provides multiple encryption options for email security, such as:
- Microsoft Purview Message Encryption
- Information rights management (IRM)
- Secure/Multipurpose Internet Mail Extensions (S/MIME)
Email encryption encodes information by transforming the email text into unreadable ciphertext, allowing only authorized recipients to decode and see/read/consume it. Email encryption works in two ways:
- In the service, encryption through TLS (used by default)
- As a customer control encryption
In the service, encryption in Microsoft 365 is used by default because it comes as a pre-set email security provision. This means you don't have to configure anything. When encrypted, nobody (interceptor) other than the intended recipient can open and read the email's information. For example, Microsoft 365 uses TLS (Transport Layer Security) to encrypt the connection or session between two servers.
#8. Data Loss Prevention (DLP) in Microsoft 365
DLP is the practice, technologies, and processes involved in protecting data loss in Office 365. Enterprises use and store sensitive information/data such as employee, financial, customer, credit card numbers, health records, social security numbers, etc. These sensitive data need protecting to reduce cyberattack risk, preventing users from unauthorized access, and preventing inappropriate data sharing.
Businesses must protect 3 types of data under DPL: data at rest, data in motion, and data in use. This can be done by the 3 types of Microsoft 365 data loss prevention capabilities: network DLP, endpoint DLP, and cloud DLP.
A strong DLP policy will help automate the process of identifying, monitoring, and protecting sensitive data/devices across different business areas, including:
- Microsoft 365 file and folder sharing tools such as SharePoint, Teams, Exchange, and OneDrive. Grant staff/third parties only the access they need to do their jobs.
- Microsoft 365 Office applications like Word, PowerPoint, Outlook Excel, Access, etc.
- Guard operating systems like Windows 10, 11, and macOS (Catalina 10.15 or higher).
- Guard on-premises SharePoint and on-premises file shares.
- Protect Third-party, non-Microsoft-based, cloud apps
Creating and managing strong DLP policies in the Microsoft 365 Compliance center help businesses stay compliant with security regulations.
#9. Advanced Threat Protection (ATP)
In Microsoft 365 Defender, there's an offer of Advanced Threat Protection (ATP) to help businesses monitor, detect and respond to advanced cybersecurity threats. Generally, ATP is an investigative response MS 365 feature for threat prevention and post-detection threats like phishing, business email compromise, etc. It also identifies and stops malicious links, websites, or email attachments before access to keep the organization's data, emails, website, and network safe from advanced threats.
ATP is an add-on in most Microsoft 365 licenses, such as the Office 365 Enterprise E5.
Microsoft 365 Plans for Your Business and ATP
In general, Microsoft 365 Business has 4 major plans with different features:
- Microsoft 365 Business Basic. It's ideal for SMBs. It comes with collaboration apps - OneDrive and SharePoint - and Office 365 classic desktop apps - Word, Excel, and PowerPoint.
- Microsoft 365 Apps for Business. Has only classic Office apps - Word, PowerPoint, Excel, Outlook, OneNote, OneDrive, Teams, Access, SharePoint, and Publisher. It gives businesses access to the apps on mobile and desktop for collaboration and productivity.
- Microsoft 365 Business Standard. Offers Microsoft 365 basic features, Microsoft 365 Apps, and Microsoft 365 cloud services. It also offers advanced services targeting specific audiences, such as professional email and online storage.
- Microsoft 365 Business Premium. This corporate plan can serve SMBs of up to 300 users. It's the best-in-class productivity suite for accessing Microsoft cloud services and has security for ATP. It also has important add-ons like Windows 365, audio conferencing, and business voice.
You need to select the right Microsoft 365 plan based on your business size, the features you want, and the security level you need.
#10. Train everyone on email best practices
Besides normal cybersecurity training, everyone in the Business needs training on email security and best practices. Why?
Email is the key target for phishing attacks and can contain malicious attacks cloaked as harmless communications. Besides, Email systems are particularly vulnerable because everyone in the Business handles email. Since safety relies on humans making consistently good decisions with this communication tool, safety and security training is important.
So, train everyone to know how and what to watch for phishing attempts, spam or junk mail, spoofing, and malware in their email.
#11. Maintain your environment
After your initial Microsoft 365 for business setup and configuration is complete, your Business needs a maintenance and operations plan to protect your data and environment. For example, as employees come and go, you'll reset passwords, add or remove users, and perhaps reset devices. Also, ensure people can access only the things/sites/data they need to do their jobs and not everything.
The important thing is to ensure that your business and operation environment is safe from attack, exposure to unauthorized access, and data loss risks.
Conclusion
Cybersecurity is an important, ever-evolving topic.
Businesses, and other organizations, store and use sensitive data that needs protection. Data and networks are often protected from employee exposure, data loss, and cyber threats.
If you're using or planning to use Microsoft's Business (any plan), these Microsoft 365 cybersecurity features we've mentioned will help you tighten your business' security and threat protection.
One more thing
Are you looking for more Microsoft 365 tips? Check out our other guides in our Blog or visit our Help Center for a wealth of information on how to troubleshoot various issues.
Sign up for our newsletter (here below) and access our blog posts, promotions, and discount codes early. Plus, you'll be the first to know about our latest guides, deals, and other exciting updates!
Related Articles for Further Reading
» Why You Should Block Microsoft Legacy Authentication
» How to Keep Your Data Safe When Using Microsoft Office 365
» Microsoft 365 Complete Review: A Review, Editions, and Prices
» Step by Step Guide to Set Up Office 365 Business Email
» Differences Between Microsoft 365 vs. Google Workspace
» Mobile Device Management (MDM) for Microsoft 365: Ultimate Guide

